 |
| The warning |
Yay! I love warnings in the event viewer. Wait, this is just a warning, "Hey, by the way I'm not replicating your crap any more and I'm not going to replicate it any more until you manually intervene." Isn't that nice? This looks like something that should be more than just a "warning."
The warning looks a bit scary, but it is very helpful in that it tells you exactly how to fix it. Have to give Microsoft points for that one, put the fix right there in the warning. I mean, you can copy and paste the command out of the warning message and into a command prompt and it'll fix itself.
Now, why exactly did I have to wade through the event viewer to find this warning and this command? Where's Clippy when you need him? A nice "Hey I noticed you didn't do a clean shutdown, would you like to re-enable your SYSVOL replication, it might be important?" Why did they neglect that? When I log back in it asks me why it was shut down improperly, why not take that same opportunity to ask about re-enabling the replication too?
But, I digress, back to fixing replication. What you ask? I'm not done yet? I told you to cut and paste the command from the event description to fix it didn't I?
If you're like me, it didn't work. I selected the text, I copied the text, I click on the Powershell prompt, waited it for it to open, I pasted the command and finally pressed enter. Only to be greeted with an "Unexpected switch at this level" message. Well that was nice and friendly. I bet I need an elevated prompt. So this time I right-clicked on the Powershell prompt and selected "Run as Administrator." Surely that will fix it, nope, it doesn't, it gives you the same error message. Ok, so I must have just not selected everything before I copied. I tried it a few more times, nothing, same error message.
Now it's time to hit the internet. I do some searching and I find this post over on howdoicomputer.com. It looks like they ran into the same problem. The trick is to use a regular command prompt, not a Powershell prompt. How do you like that? The answer's right in the event message, "from an elevated command prompt." So Microsoft's be all end all Powershell prompt is useless when it comes to using this WMI command.
I also ran into the DFSR error 4012 that they mention in that same post over at howdoicomputer.com.
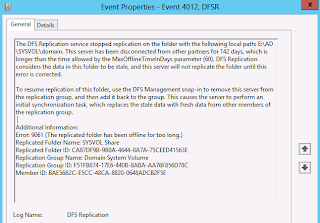 |
| The error |
By default, you've only got 60 days to correct the problem, after that it will not restart replication. The quick fix for that is to change that default window to something greater than however many days you have been out of replication and then run the command again. The command for increasing that default is:
wmic.exe /namespace:\\root\microsoftdfs path DfsrMachineConfig set MaxOfflineTimeInDays=200
That 200 on the end is the number of days to increase it to (you can pick anything above how many days you're out).. I'm a bit embarrassed to admit, that I had run substantially longer than the 60 day default (you can see in the screenshot) and had to increase it a lot to get it to run. However, when I finished I did set it back its default of 60 days.
When it's all said and done you should get a Information event from ID 2214 that says the replication service successfully recovered.
 |
| It's fixed! |